Rash Detection App Data Security: Protecting Your Privacy
Ensure your privacy with robust security in rash detection apps. Learn about encryption, compliance, and best practices for safe data handling.

Estimated reading time: 7 minutes
Key Takeaways
- AI-driven analysis must be paired with robust data protection to earn user trust.
- Key risks include unauthorized access, insecure storage, data misuse, and opaque policies.
- Best practices: AES-256 & TLS 1.2+, HTTPS with certificate pinning, MFA, biometrics, and regular audits.
- Compliance with HIPAA, GDPR, and local laws not only avoids penalties but also boosts credibility.
- Users should vet privacy policies, use strong passwords, and limit data sharing to guard their own health data.
Table of Contents
- I. Introduction
- II. How Rash Detection Apps Work
- III. The Importance of Data Security in Healthcare Apps
- IV. Common Privacy and Data Security Concerns
- V. Best Practices for Ensuring Data Security
- VI. Regulatory Frameworks and Compliance Requirements
- VII. User-Focused Guidance
- VIII. Summary & Call to Action
I. Introduction
Rash detection apps are AI-powered mobile or web tools that identify or explain skin rashes from photos. They combine image analysis, machine learning, and user data to give on-demand analysis with the AI Rash Detector App. These digital health tools let people get guidance at home or prepare for doctor visits.
Digital health is growing fast. More users rely on on-demand rash detection apps for quick, convenient advice. But this convenience comes with a duty: keep images, personal health details, and metadata safe.
“Rash detection app data security” means the protocols and safeguards that protect your photos, medical history, and related data. Strong data security builds user trust, meets legal rules, and stops leaks of sensitive health information.
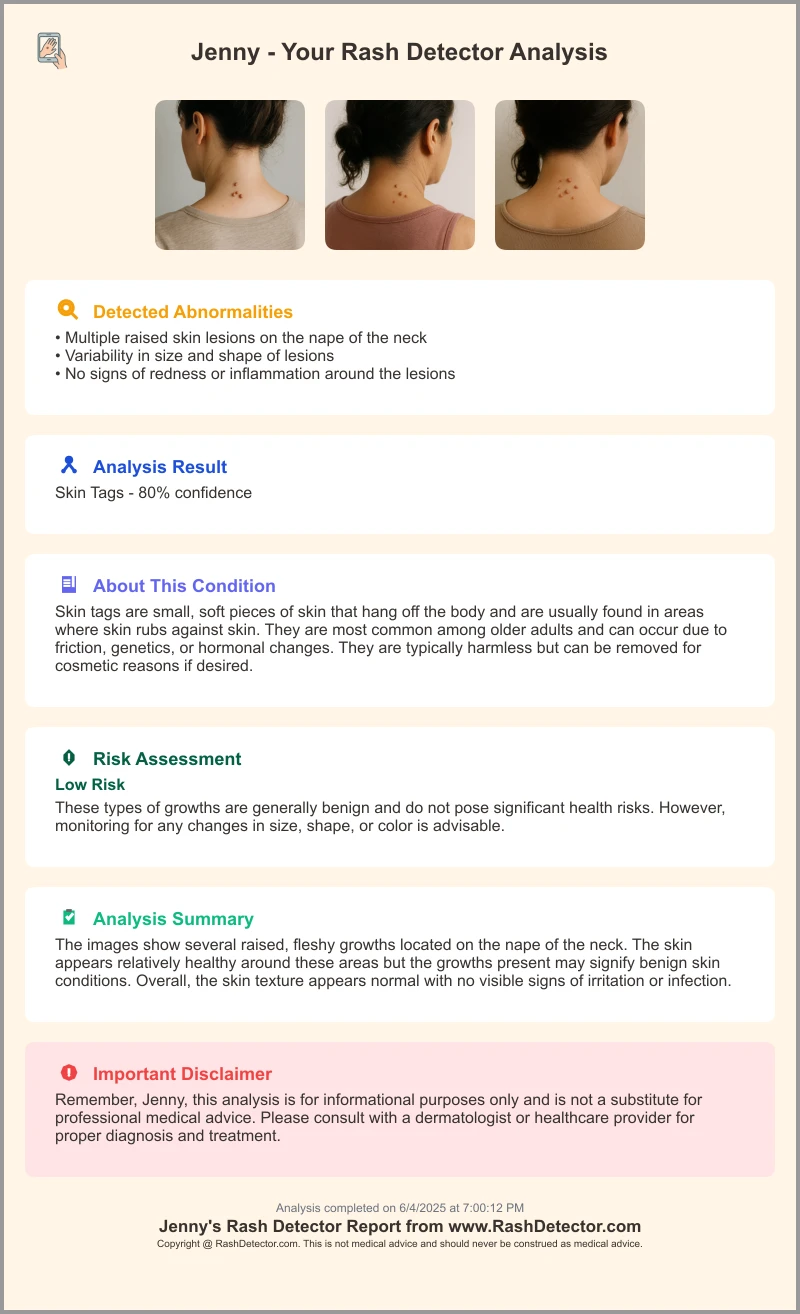
Tools like Rash Detector use robust encryption standards, strict access controls, and transparent policies to safeguard user data. Below is a sample report layout demonstrating how findings are presented securely:
II. How Rash Detection Apps Work
A. Data Collection Workflow- Step 1: User takes or uploads a photo of the affected skin.
- Step 2: User answers questions on skin type, duration, symptoms, and location.
- Convolutional Neural Networks (CNNs) are machine-learning models trained on thousands of dermoscopic images via How AI Diagnoses Rashes.
- The AI compares the user’s photo to its database, examining color, shape, and texture.
- Continuous learning: anonymized images and survey answers feed back into the model to improve accuracy.
- Anonymized data may be used to refine algorithms or for medical research.
- User consent is required before any sharing of personal or health information.
- Apps must explain how data is stored, used, and if it’s shared outside the company.
III. The Importance of Data Security in Healthcare Apps
A. Sensitivity of Health Data- Medical images and health history rank as “highly sensitive” under most privacy laws.
- Photos of rashes can reveal treatment details or underlying conditions.
- Loss of User Trust: Users will abandon apps if they fear leaks.
- Reputational Damage: Developers can face public backlash and loss of market share.
- Legal Penalties: Fines under HIPAA or GDPR can reach millions of dollars.
- Personal Harm: Exposed data can lead to identity theft or health discrimination.
Strong data security is not optional. It’s a core design feature that protects both users and developers.
IV. Common Privacy and Data Security Concerns
A. Unauthorized Access- Weak passwords or missing multi-factor authentication let hackers into accounts.
- Stolen credentials can expose private images and medical history.
- Data “at rest” on servers or devices must be encrypted.
- Without encryption, stolen servers or lost devices reveal raw data.
- Some apps may sell or share user data with advertisers or analytics firms.
- Users often don’t see these clauses buried in long privacy policies.
- Users may not know how long data is kept, where it travels, or with whom it’s shared.
- Without clear communication, consent isn’t truly informed.
Addressing these concerns requires technical measures, clear policies, and user education.
V. Best Practices for Ensuring Data Security
A. Encryption Standards- Data at Rest: Use AES-256 to lock data on servers and devices.
- Data in Transit: Enforce TLS 1.2 or higher for all network communications.
- Example: Aysa keeps photos on the device by default; users opt in to share images with the cloud.
- Always use HTTPS with valid SSL/TLS certificates.
- Implement certificate pinning to block man-in-the-middle attacks.
- Require Multi-Factor Authentication (MFA) for user and admin accounts.
- Support biometric locks (fingerprint, Face ID) for app access.
- Implement role-based access control (RBAC) within the development team.
- Conduct quarterly penetration tests and code reviews.
- Use automated vulnerability scanning tools on every code commit.
- Patch critical vulnerabilities within 48 hours of discovery.
Implementing these practices turns data security from a promise into action.
VI. Regulatory Frameworks and Compliance Requirements
A. HIPAA (U.S.)- PHI (Protected Health Information) includes images, diagnoses, and contact info.
- Technical Safeguards: encryption, audit controls, user authentication, and transmission security.
- Data Minimization: collect only what’s necessary.
- Explicit Consent: users must opt in to data collection.
- Right to be Forgotten: users can request data deletion.
- Data Portability: users can transfer their data to another provider.
- Canada’s PIPEDA, Australia’s Privacy Act, Brazil’s LGPD—all have similar rules.
- Developers must check local health-data regulations before launch.
- Builds user confidence and trust.
- Reduces risk of fines and lawsuits.
- Creates a market differentiator—“fully compliant” solutions.
VII. User-Focused Guidance
A. How to Evaluate an App’s Privacy Stance- Read the Privacy Policy: look for clear statements on data collection, storage, and sharing.
- Check Compliance Badges: HIPAA- or GDPR-compliant seals build trust.
- Review Security Features: see if MFA, encryption, or biometrics are supported.
- Upload Only What’s Needed: crop images to show just the rash, not background cues.
- Update Apps Promptly: new versions fix security bugs.
- Use Strong, Unique Passwords: employ passphrases or password managers.
- Enable Biometrics: Face ID or fingerprint adds a security layer.
- Review App Permissions: disable camera or storage access when not needed.
By adopting these habits, users strengthen the security of their own health data.
VIII. Summary & Call to Action
- Rash detection apps use AI, CNNs, and user questionnaires to analyze skin conditions on demand.
- Protecting user images, health details, and metadata is crucial for building trust and meeting legal requirements.
- Common risks include unauthorized access, insecure storage, data misuse, and unclear policies.
- Best practices involve strong encryption, HTTPS with certificate pinning, MFA, biometrics, and regular audits.
- Compliance with HIPAA, GDPR, and local laws reduces legal risk and boosts credibility.
- Users should vet privacy policies, update apps, use strong passwords, and limit data sharing.
Call to Action: Developers and stakeholders must prioritize rash detection app data security. Users should choose apps that commit to strong encryption, transparent policies, and regulatory compliance. Together, we can unlock the full potential of digital skin-health tools—confident that personal data remains safe and private.
FAQ
Q: How can I be sure my rash photos are stored securely?
A: Look for apps that use end-to-end encryption (AES-256 at rest, TLS 1.2+ in transit), enforce multi-factor authentication, and publish third-party audit reports.
Q: What regulations should my app comply with?
A: In the U.S., HIPAA covers Protected Health Information. In the EU, GDPR governs personal data. Other regions—PIPEDA, LGPD, Privacy Act—apply locally.
Q: Can I delete my data if I change my mind?
A: Yes. GDPR’s Right to be Forgotten and many privacy policies allow users to request full data deletion. Always check the app’s data-retention policy.
Q: What should I do if I suspect a breach?
A: Immediately change your password, enable multi-factor authentication, and contact the app’s support or compliance team to report the incident.





