The Critical Role of Data Encryption in Dermatology Apps
Discover the importance of data encryption in dermatology apps for secure rash detection, ensuring compliance and user privacy while building trust.

Estimated reading time: 8 minutes
Key Takeaways
- Data encryption is essential for protecting sensitive skin-health data in teledermatology apps.
- End-to-end encryption and AES-256 at rest uphold HIPAA and GDPR compliance.
- Balancing robust security with seamless user experience boosts patient trust and engagement.
- Emerging methods like homomorphic encryption and quantum-resistant algorithms are the next frontier.
Table of Contents
- Overview of Dermatology and Rash Detection Apps
- Importance of Data Encryption
- End-to-End Encryption and Secure Storage
- HIPAA and GDPR: Privacy and Data Security
- Balancing Security and User Experience
- Case Study: Teledermatology Platforms
- Future Trends in Encryption
- Conclusion
- Call to Action
- FAQ
1. Overview of Dermatology Apps and Rash Detection Apps
Dermatology apps offer mobile solutions for diagnosing and managing skin conditions. Rash detection apps—powered by AI and machine learning—analyze high-resolution images to identify rashes, log symptoms, and facilitate teleconsultations. Common personal health information (PHI) collected includes:
- Skin photos (JPEG, PNG)
- Medical history and allergies
- User identity details (name, age, email)
- Prescription and follow-up notes
The sensitivity and volume of this data make encryption a non-negotiable requirement from day one. Protecting pixel data and personal records preserves user confidentiality and ensures legal compliance.
2. Importance of Data Encryption in Dermatology Apps
Encryption converts readable health records into ciphertext accessible only by authorized parties. Key benefits include:
- Protection of PHI under HIPAA and GDPR requirements
- Defense against man-in-the-middle attacks during image uploads
- Assurance of data integrity, preventing tampering
- Enhanced patient trust, encouraging accurate reporting
Strong cryptographic protocols and secure key management prevent data leaks and reinforce a commitment to privacy and safety. Source: ConsentZ
3. End-to-End Encryption and Secure Storage
Implementing multi-layered encryption involves:
- End-to-End Encryption:
- Device-level encryption at capture
- TLS/SSL for encrypted transit
- Clinician-only decryption keys
- Secure Data Storage:
- AES-256 encryption-at-rest on cloud servers
- Segregated encrypted databases for health images
- HSM-based key vaults for cryptographic keys
Common protocols:
- AES – Symmetric block cipher with 128- or 256-bit keys (NIST-approved).
- RSA – Asymmetric for secure key exchange and digital signatures.
4. HIPAA and GDPR: Privacy and Data Security
Regulatory frameworks demand strong safeguards:
- HIPAA – Encryption is an “addressable” Security Rule measure; breach notification for incidents affecting over 500 individuals.
- GDPR – “Data protection by design and default” mandates encryption at all stages, plus secure deletion and portability.
Encrypted ciphertext remains unreadable if intercepted, minimizing breach impacts and showcasing proactive privacy measures. Source: Rash Detector Privacy
5. Balancing Security and User Experience
Strong encryption must integrate seamlessly:
- Biometric Login: Fingerprint or Face ID for instant access
- Hardware-Accelerated Encryption: AES offloading to device co-processors
- Session Caching: Temporary key caching to reduce repeated prompts
- Transparent Privacy Prompts: Plain-language explanations of security benefits
By making encryption invisible, developers preserve a smooth journey while protecting sensitive information.
6. Case Study: Data Encryption in Teledermatology
Verified Medical
- End-to-end encryption of patient images and clinical notes
- AES-256 at rest on HIPAA-certified cloud
- Role-based access control
Skinive
- Device encryption isolating photos
- TLS 1.3 for secure transfer
- Automated key rotation every 90 days
7. Homomorphic Encryption and Future Trends
Advanced techniques on the horizon:
- Homomorphic Encryption: AI analysis on encrypted data without decryption
- Quantum-Resistant Algorithms: Lattice-based cryptography to counter future threats
- Secure Multi-Party Computation: Collaborative diagnostics while preserving data confidentiality
Early adoption of these methods will set new benchmarks. Source: NIST post-quantum cryptography initiatives
8. Conclusion: Data Encryption in Dermatology Apps
Robust encryption—from AES-256 to end-to-end tunnels—ensures compliance, mitigates breach risks, and fosters patient trust. As threats evolve, homomorphic methods and quantum-safe schemes will be vital. Strengthening encryption today paves the way for secure, user-friendly teledermatology tomorrow.
For a practical glimpse, see the sample report generated by Rash Detector.
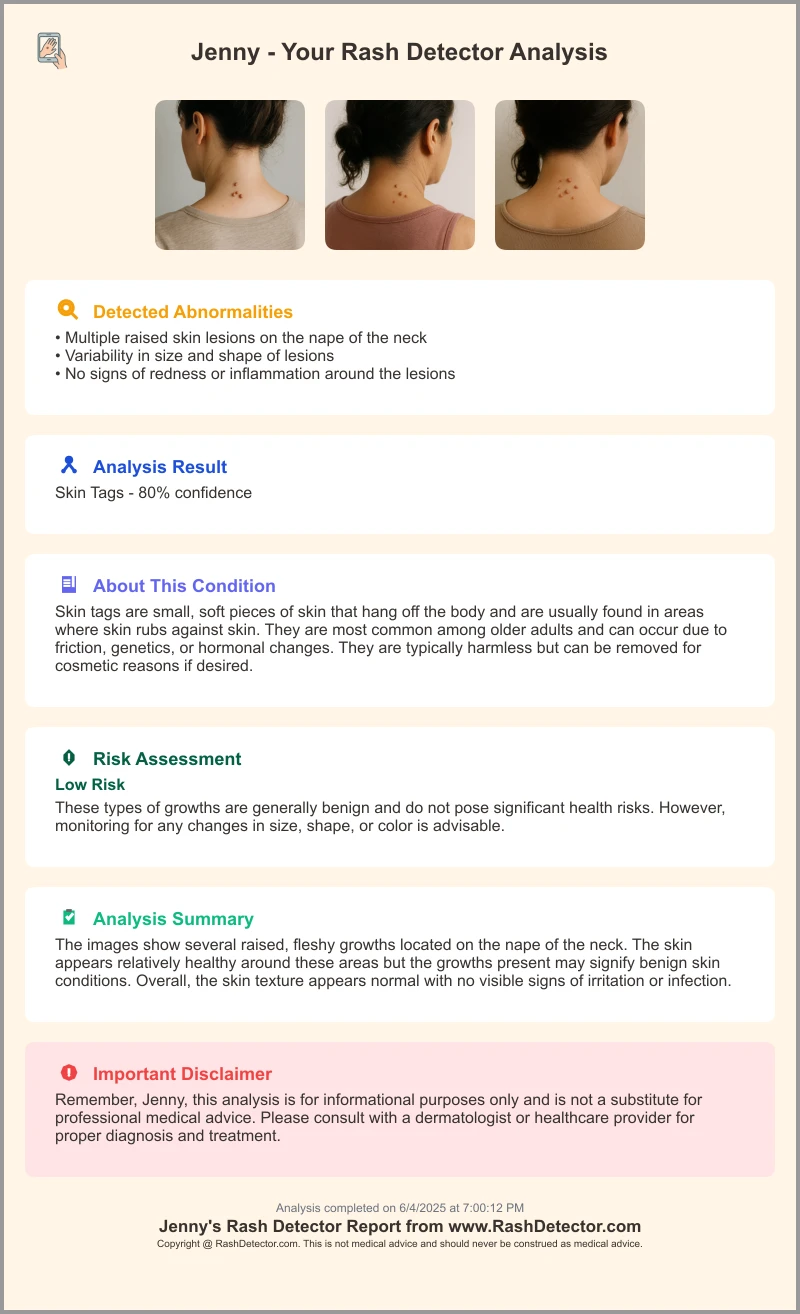
9. Call to Action: Healthcare Data Security
What are your experiences or concerns about data privacy in dermatology or rash detection apps? Share your thoughts in the comments below.
Further Reading:
FAQ
- Why is encryption critical in dermatology apps?
It protects sensitive PHI—like skin photos and medical history—from unauthorized access and ensures regulatory compliance. - What is AES-256?
Advanced Encryption Standard with 256-bit keys, used to secure data at rest in cloud servers. - How does end-to-end encryption work?
Data is encrypted on the user’s device, transmitted securely via TLS/SSL, and only decrypted by authorized clinicians. - Can encryption affect app performance?
Minimal latency can occur, but hardware-accelerated encryption and session caching mitigate delays. - What future encryption trends should I watch?
Homomorphic encryption, quantum-resistant algorithms, and secure multi-party computation are emerging solutions.





